S
Susan Lamatrice
Guest
Our recent webinar, Enterprise Security in Data Access, gives a detailed look at security options and implementations in the data access landscape. Security is of particular interest to those using hybrid environments where data and/or applications reside in a combination of cloud and on-premises locations.
Security in Data Connectivity
As the premier data connectivity vendor for enterprises, DataDirect often fields questions on designing a plan for data security. Because thousands of corporations and software vendors use our connectivity solutions, we also get many questions about how DataDirect designs, implements and tests security in our development environment.
For more on this topic, let’s meet Jim Silhavy. Jim manages ODBC and JDBC driver development at Progress and previously was a JDBC driver and ADO.NET provider developer. Jim holds two patents related to making single sign-on authenticated database connections from a database driver.
Let’s discuss some frequently asked questions that Jim addressed on our recent webinar.

Interview with Jim Silhavy
Jim, with the ongoing rash of data breaches and data security topics in the news, implementing a crucial piece of connectivity must scare both corporate clients and software vendors. How do you get customers and prospects comfortable with the security of DataDirect products?
Jim Silhavy: Security is a differentiator for us, and we want to keep it that way. Our Service Organization Control (SOC2) certification attests to that. First, it gives our customers confidence by providing a transparent view into our organization. Data access is obviously a critical function. If it’s not done right, problems will find their way into our customer’s world. Second, it helps our customers meet their vendor due diligence expectations. Most customers are regulated by someone, they can’t just do business with a vendor without questions being asked about their security. Another differentiator is our experience. We’ve been testing connectors for over two decades. During that time, we’ve created a security-minded development culture with a history of testing breadth that’s really unparalleled. I’d encourage folks to watch the webinar for details on the specifics of our testing environments.
What are the components of a comprehensive enterprise data security implementation?
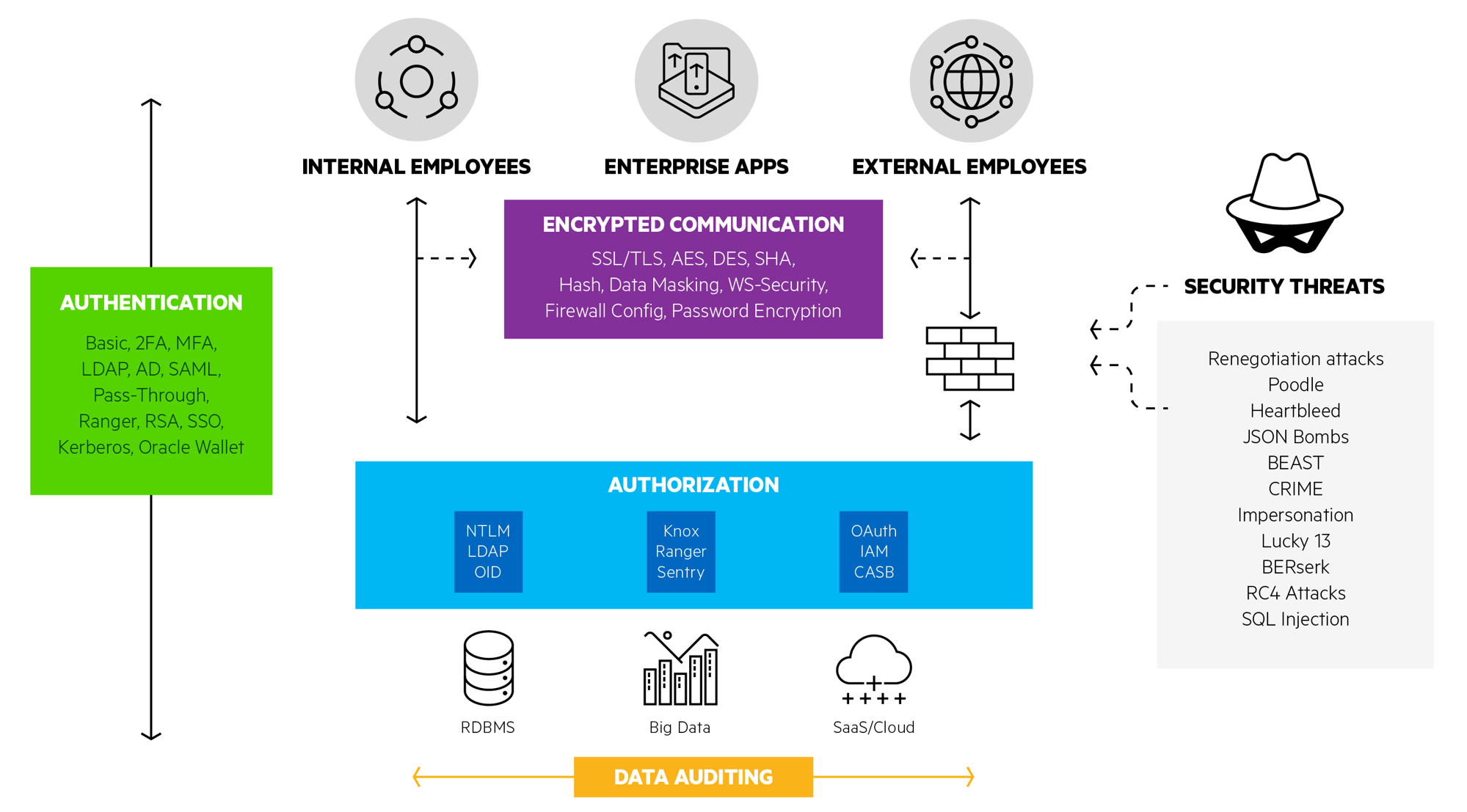
Jim Silhavy: Here’s a pictorial representation of the complexity of data access security. At the top, you have applications that you’re building and managing. At the bottom, you have the goal: accessing data. Along the way are all the elements of data access security. As you can see, there are a substantial number of distributed technologies required. You must identify that the client is who or what they claim to be, noted in green. You must determine what data and actions are accessible to the client, noted in blue. You must secure the data as it moves by means of encryption, noted in purple. And you must monitor and/or trace access and movement as it occurs, noted in orange. Identifying and coordinating the use of these technologies in a manner that’s safe from security threats is, of course, the challenge that we all face.
Is DataDirect compliant with U.S. government security requirements for software?
Jim Silhavy: We recently introduced FIPS 140-2 compliance, and features to support FedRAMP compliance (for example, account lockout policies) to our Hybrid Data Pipeline product. In addition, we are SOC2 certified. Our SOC2 certification was obtained from an independent auditor and attests to both our technical and operational maturity. The certification was not easy to do. It can be painful, but we put ourselves through that to demonstrate that we have internal controls in place to meet industry best practices.
Are there specific tools or processes that you recommend for ongoing security checks?
Jim Silhavy: VeraCode is a widely used and respected industry tool for finding vulnerabilities that can lead to cybersecurity breaches or hacking attempts. Static code analysis tools like Prefast are used to find serious defects (like crashes) and germane to our conversation, exploitable security holes caused by memory management, pointer management, initialization and boundary violations. Fuzz testing is an automated testing software technique that involves providing invalid, unexpected or random data as inputs to a computer program. At DataDirect we implement all of these tools and more. For example, we’ve developed a tool for internal use that scans memory during testing to ensure that passwords provided to our drivers do not exist in memory in cleartext format.
What happens when security breaches do happen, such as the recent Heartbleed, POODLE and FREAK breaches in the news?
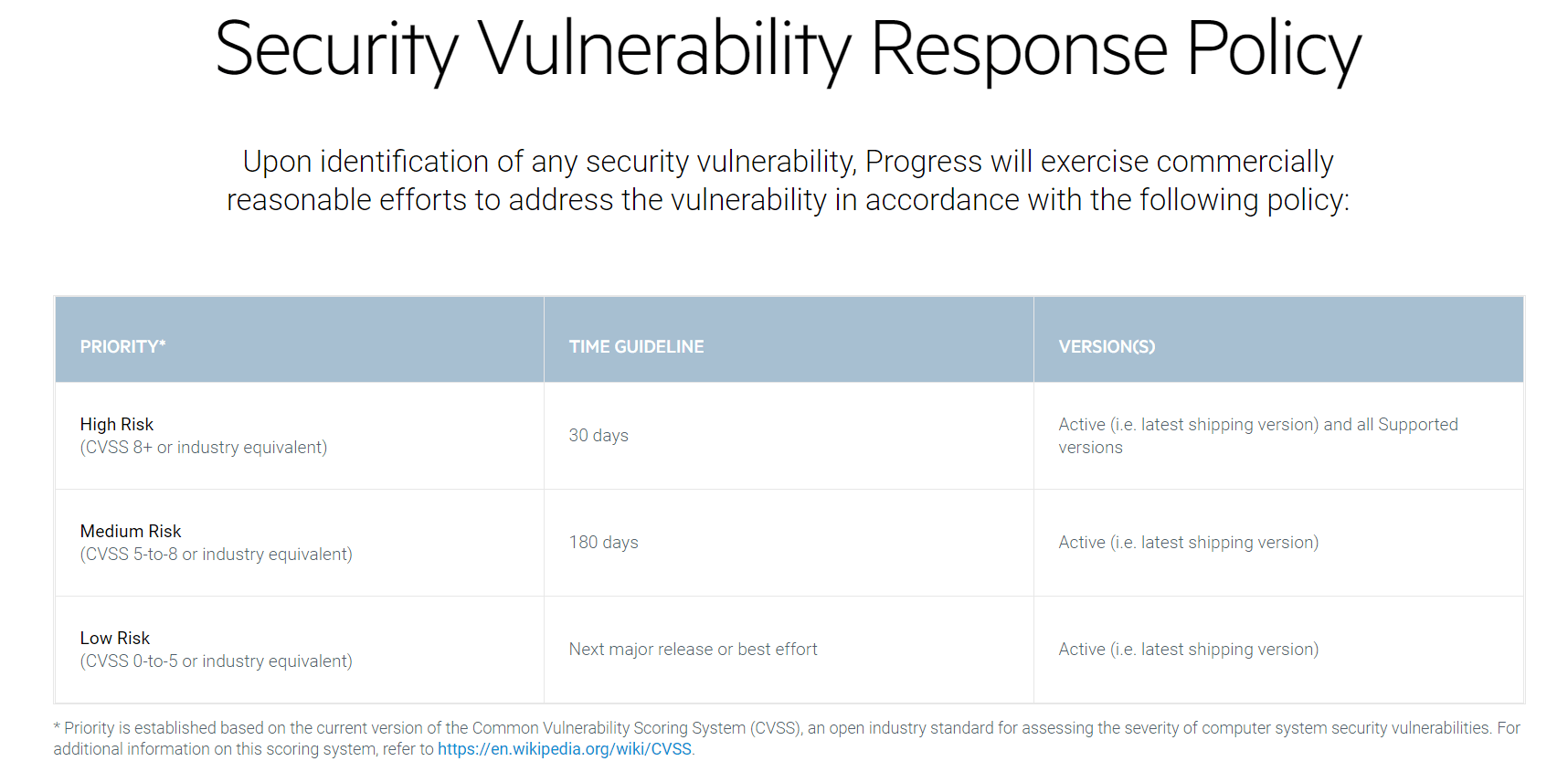
Jim Silhavy: To satisfy the stringent requirements of our customer base, we’ve crafted a proactive Security Vulnerability Response Policy. For example, high risks are patched within 30 days for all supported versions. It’s another way we can boost our customers’ confidence in the data solutions we provide.
Jim, thanks so much for your time. For more comprehensive details on Enterprise Data Security and on DataDirect’s security approach, watch the full webinar.
View Webinar
Continue reading...
Security in Data Connectivity
As the premier data connectivity vendor for enterprises, DataDirect often fields questions on designing a plan for data security. Because thousands of corporations and software vendors use our connectivity solutions, we also get many questions about how DataDirect designs, implements and tests security in our development environment.
For more on this topic, let’s meet Jim Silhavy. Jim manages ODBC and JDBC driver development at Progress and previously was a JDBC driver and ADO.NET provider developer. Jim holds two patents related to making single sign-on authenticated database connections from a database driver.
Let’s discuss some frequently asked questions that Jim addressed on our recent webinar.

Interview with Jim Silhavy
Jim, with the ongoing rash of data breaches and data security topics in the news, implementing a crucial piece of connectivity must scare both corporate clients and software vendors. How do you get customers and prospects comfortable with the security of DataDirect products?
Jim Silhavy: Security is a differentiator for us, and we want to keep it that way. Our Service Organization Control (SOC2) certification attests to that. First, it gives our customers confidence by providing a transparent view into our organization. Data access is obviously a critical function. If it’s not done right, problems will find their way into our customer’s world. Second, it helps our customers meet their vendor due diligence expectations. Most customers are regulated by someone, they can’t just do business with a vendor without questions being asked about their security. Another differentiator is our experience. We’ve been testing connectors for over two decades. During that time, we’ve created a security-minded development culture with a history of testing breadth that’s really unparalleled. I’d encourage folks to watch the webinar for details on the specifics of our testing environments.
What are the components of a comprehensive enterprise data security implementation?
Jim Silhavy: Here’s a pictorial representation of the complexity of data access security. At the top, you have applications that you’re building and managing. At the bottom, you have the goal: accessing data. Along the way are all the elements of data access security. As you can see, there are a substantial number of distributed technologies required. You must identify that the client is who or what they claim to be, noted in green. You must determine what data and actions are accessible to the client, noted in blue. You must secure the data as it moves by means of encryption, noted in purple. And you must monitor and/or trace access and movement as it occurs, noted in orange. Identifying and coordinating the use of these technologies in a manner that’s safe from security threats is, of course, the challenge that we all face.

Is DataDirect compliant with U.S. government security requirements for software?
Jim Silhavy: We recently introduced FIPS 140-2 compliance, and features to support FedRAMP compliance (for example, account lockout policies) to our Hybrid Data Pipeline product. In addition, we are SOC2 certified. Our SOC2 certification was obtained from an independent auditor and attests to both our technical and operational maturity. The certification was not easy to do. It can be painful, but we put ourselves through that to demonstrate that we have internal controls in place to meet industry best practices.
Are there specific tools or processes that you recommend for ongoing security checks?
Jim Silhavy: VeraCode is a widely used and respected industry tool for finding vulnerabilities that can lead to cybersecurity breaches or hacking attempts. Static code analysis tools like Prefast are used to find serious defects (like crashes) and germane to our conversation, exploitable security holes caused by memory management, pointer management, initialization and boundary violations. Fuzz testing is an automated testing software technique that involves providing invalid, unexpected or random data as inputs to a computer program. At DataDirect we implement all of these tools and more. For example, we’ve developed a tool for internal use that scans memory during testing to ensure that passwords provided to our drivers do not exist in memory in cleartext format.
What happens when security breaches do happen, such as the recent Heartbleed, POODLE and FREAK breaches in the news?
Jim Silhavy: To satisfy the stringent requirements of our customer base, we’ve crafted a proactive Security Vulnerability Response Policy. For example, high risks are patched within 30 days for all supported versions. It’s another way we can boost our customers’ confidence in the data solutions we provide.

Jim, thanks so much for your time. For more comprehensive details on Enterprise Data Security and on DataDirect’s security approach, watch the full webinar.
View Webinar
Continue reading...
